Download CyberArk Endpoint Privilege Manager.EPM-DEF.ExamTopics.2025-12-27.124q.vcex
| Vendor: | CyberArk |
| Exam Code: | EPM-DEF |
| Exam Name: | CyberArk Endpoint Privilege Manager |
| Date: | Dec 27, 2025 |
| File Size: | 646 KB |
| Downloads: | 2 |
How to open VCEX files?
Files with VCEX extension can be opened by ProfExam Simulator.
Discount: 20%
Demo Questions
Question 1
What is the main reason to use the custom user access token for Elevate policies?
- to provide more privileges of permissions for the user
- to implement a less strict set of permissions for the user
- to provide least privileges of permissions for the user
- to impersonate the user with another set of permissions
Correct answer: D
Question 2
What is default retention period for admin activities on the web console?
- 14 days
- 30 days
- 90 days
- 1 year
Correct answer: B
Question 3
Refer to the exhibit.
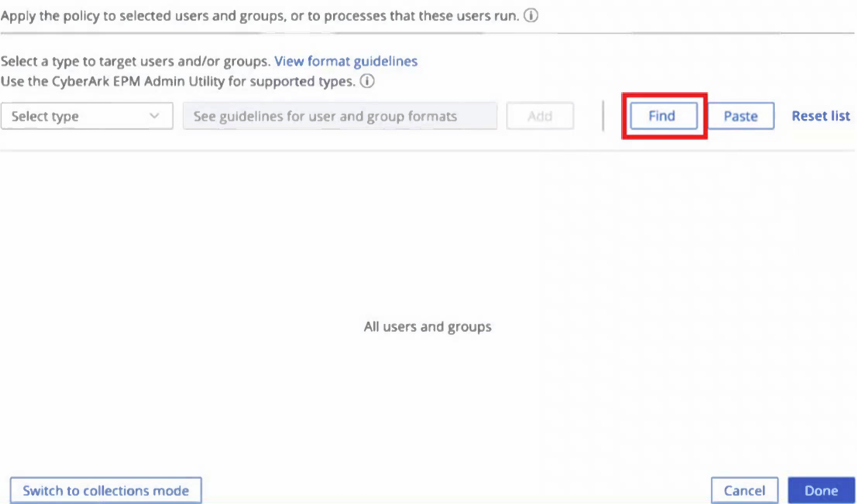
When editing an application policy, what does the "Find" button do?
- It opens all users and groups in EPM console
- It opens CyberArk Software to check if the connection with AD is working
- In the EPM admin utility, it opens a window to select users and group from AD or from the local endpoint
- In the EPM admin utility, it opens a page in the EPM console for you to select the users or group
Correct answer: C
Question 4
How many days after license expiration do EPM agents stop enforcing policies?
- 1
- 14
- 30
- 120
Correct answer: C
Question 5
When adding the EPM agent to a pre-existing security stack on workstation, what two steps are CyberArk recommendations. (Choose two.)
- Add any pre-existing security application to the Files to Be Ignored Always.
- Add EPM agent to the other security tools exclusions.
- EPM agent should never be run with any other security tools.
- Create new advanced policies for each security tool.
Correct answer: AB
Question 6
For the CyberArk EPM Threat Deception Credential Lure feature, what is the recommendation regarding the username creation?
- The username should match to an existing account.
- The username should have a strong password associated.
- The username should not match to an existing account.
- The username should match the built-in local Administrator.
Correct answer: C
Question 7
CyberArk EPM's Ransomware Protection comes with file types to be protected out of the box. If an EPM Administrator would like to remove a file type from Ransomware Protection, where can this be done?
- Policy Scope within Protect Against Ransomware
- Authorized Applications (Ransomware Protection) within Application Groups
- Set Security Permissions within Advanced Policies
- Protected Files within Agent Configurations
Correct answer: A
Question 8
When blocking applications, what is the recommended practice regarding the end-user UI?
- Show a block prompt for blocked applications.
- Show no prompts for blocked applications.
- Hide the CyberArk EPM Agent icon in the system tray.
- Enable the Default Deny policy.
Correct answer: A
Question 9
What is required to configure SAML authentication on EPM?
- OAuth token
- Signed Authentication Request
- Encrypted Assertion
- Signed SAML Response
Correct answer: B
Question 10
An EPM Administrator is looking to enable the Threat Deception feature, under what section should the EPM Administrator go to enable this feature?
- Threat Protection Inbox
- Policies
- Threat Intelligence
- Policy Audit
Correct answer: B
Question 11
A policy needs to be created to block particular applications for a specific user group. Based on CyberArk's policy naming best practices, what should be included in the policy's name?
- Policy creation date
- Target use group
- Creator of the policy
- The policy's Set name
Correct answer: B
Question 12
After a clean installation of the EPM agent, the local administrator password is not being changed on macOS and the old password can still be used to log in.
What is a possible cause?
- Secure Token on macOS endpoint is not enabled.
- EPM agent is not able to connect to the EPM server.
- After installation, Full Disk Access for the macOS agent to support EPM policies was not approved.
- Endpoint password policy is too restrictive.
Correct answer: A
Question 13
For Advanced Policies, what can the target operating system users be set to?
- Local or AD users and groups, Azure AD User, Azure AD Group
- AD Groups, Azure AD Groups
- Local or AD users and groups
- Local or AD users, Azure AD Users
Correct answer: C
Question 14
In EPM, creation of which user type is required to use SAML?
- Local CyberArk EPM User
- AD User
- SQL User
- Azure AD User
Correct answer: A
Question 15
What are the predefined application groups?
- Developer group, Administrator group
- Run as Administrator, Run as Developer, Block
- Elevate, Allow, Block, Developer Applications
- Block Only
Correct answer: C
Question 16
Which policy can be used to improve endpoint performance for applications commonly used for software development?
- Developer Applications
- Trusted Application
- Trusted Source
- Software Updater
Correct answer: B
Question 17
Where would an EPM admin configure an application policy that depends on a script returning true for an end user's machine being connected to an open (no password protection) Wi-Fi?
- Advanced Policy - Application Control - Check Wi-Fi security
- Advanced Policy - Options: Conditional enforcement - Apply Policy according to Script execution result
- Default policies - Check if network access is secure
- Advanced Policy - Access - Specify permissions to be set for Wi-Fi network security
Correct answer: B
Question 18
When deploying Ransomware Protection, what tasks should be considered before enabling this functionality? (Choose two.)
- Add trusted software to the Authorized Applications (Ransomware protection) Application Group
- Add trusted software to the Allow Application Group
- Add additional files, folders, and/or file extensions to be included to Ransomware Protection
- Enable Detect privileged unhandled applications under Default Policies
Correct answer: AC
Question 19
How does EPM help streamline security compliance and reporting?
- Use of automated distribution of reports to the security team
- Provides reports in standard formats such as PDF, Word and Excel
- Print reports
- Create custom reports
Correct answer: B
Question 20
Before enabling Ransomware Protection, what should the EPM Administrator do first?
- Enable the Privilege Management Inbox in Elevate mode.
- Enable the Control Applications Downloaded From The Internet feature in Restrict mode.
- Review the Authorized Applications (Ransomware Protection) group and update if necessary.
- Enable Threat Protection and Threat Intelligence modules.
Correct answer: C
Question 21
When working with credential rotation/loosely connected devices, what additional CyberArk components are required?
- PTA
- ОРМ
- PVWA
- DAP
Correct answer: C
Question 22
When enabling Threat Protection policies, what should an EPM Administrator consider? (Choose two.)
- Some Threat Protection policies are applicable only for Windows Servers as opposed to Workstations.
- Certain Threat Protection policies apply for specific applications not found on all machines.
- Threat Protection policies requires an additional agent to be installed.
- Threat Protection features are not available in all regions.
Correct answer: AB
Question 23
Which programming interface enables you to perform activities on EPM objects via a REST Web Service?
- EPM Web Services SDK
- Application Password SDK
- Mac Credential Provider SDK
- Java password SDK
Correct answer: A
Question 24
What is a valid step to investigate an EPM agent that is unable to connect to the EPM server?
- On the end point, open a browser session to the URL of the EPM server.
- Ping the endpoint from the EPM server.
- Ping the server from the endpoint.
- Restart the end point
Correct answer: C
Question 25
Which EPM reporting tool provides a comprehensive view of threat detection activity?
- Threat Detection Dashboard
- Detected Threats
- Threat Detection Events
- McAfee ePO Reports
Correct answer: A
Question 26
Select the default threat intelligence source that requires additional licensing.
- VirusTotal
- Palo Alto WildFire
- CyberArk Application Risk Analysis Service
- NSRL
Correct answer: B
Question 27
What can you manage by using User Policies?
- Just-In-Time endpoint access and elevation, access to removable drives, and Services access.
- Access to Windows Services only.
- Filesystem and registry access, access to removable drives, and Services access.
- Just-In-Time endpoint access and elevation, access to removable drives, filesystem and registry access, Services access, and User account control monitoring.
Correct answer: D
Question 28
A particular user in company ABC requires the ability to run any application with administrative privileges every day that they log in to their systems for a total duration of 5 working days.
What is the correct solution that an EPM admin can implement?
- An EPM admin can generate a JIT access and elevation policy with temporary access timeframe set to 120 hours
- An EPM admin can generate a JIT access and elevation policy with temporary access timeframe set to 120 hours and Terminate administrative processes when the policy expires option unchecked
- An EPM admin can create an authorization token for each application needed by running: EPMOPAGtool.exe -command gentoken -targetUser <username> -filehash <file hash> -timeLimit 120 -action run
- An EPM admin can create a secure token for the end user's computer and instruct the end user to open an administrative command prompt and run the command vfagent.exe -UseToken <securetoken_value>
Correct answer: B
Question 29
A company is looking to manage their Windows Servers and Desktops with CyberArk EPM. Management would like to define different default policies between the Windows Servers and Windows Desktops.
What should the EPM Administrator do?
- In the Default Policies, exclude either the Windows Servers or the Windows Desktops.
- Create Advanced Policies to apply different policies between Windows Servers and Windows Desktops.
- CyberArk does not recommend installing EPM Agents on Windows Servers.
- Create a separate Set for Windows Servers and Windows Desktops.
Correct answer: B
Question 30
An EPM Administrator would like to enable a Threat Protection policy, however, the policy protects an application that is not installed on all endpoints.
What should the EPM Administrator do?
- Enable the Threat Protection policy and configure the Policy Targets.
- Do not enable the Threat Protection policy.
- Enable the Threat Protection policy only in Detect mode.
- Split up the endpoints in to separate Sets and enable Threat Protection for only one of the Sets.
Correct answer: D
Question 31
An EPM Administrator would like to enable CyberArk EPM's Ransomware Protection in Restrict mode. What should the EPM Administrator do?
- Set Block unhandled applications to On.
- Set Protect Against Ransomware to Restrict.
- Set Protect Against Ransomware to Restrict and Set Block unhandled applications to On.
- Set Control unhandled applications to Detect.
Correct answer: C
Question 32
CyberArk's Privilege Threat Protection policies are available for which Operating Systems? (Choose two.)
- Windows Workstations
- Windows Servers
- MacOS
- Linux
Correct answer: AB
Question 33
Where can you view CyberArk EPM Credential Lures events?
- Application Catalog
- Threat Protection Inbox
- Events Management
- Policy Audit
Correct answer: B
Question 34
Which of the following is CyberArk's Recommended FIRST roll out strategy?
- Implement Application Control
- Implement Privilege Management
- Implement Threat Detection
- Implement Ransomware Protection
Correct answer: B
Question 35
Which of the following application options can be used when defining trusted sources?
- Publisher, Product, Size, URL
- Publisher, Name, Size, URI
- Product, URL, Machine, Package
- Product, Publisher, User/Group, Installation Package
Correct answer: D
Question 36
Which setting in the agent configuration controls how often the agent sends events to the EPM Server?
- Event Queue Flush Period
- Heartbeat Timeout
- Condition Timeout
- Policy Update Rate
Correct answer: A
Question 37
An EPM Administrator needs to create a policy to allow the MacOS developers elevation to an application. What type of policy should be used?
- Elevate Application Group
- Developer Applications Application Group
- Elevate Trusted Applications If Necessary Advanced Policy
- Elevate MacOS Policy
Correct answer: D
Question 38
When working with credential rotation at the EPM level, what is the minimum time period that can be set between connections?
- 1 hour
- 5 hours
- 24 hours
- 72 hours
Correct answer: B
Question 39
An EPM Administrator would like to include a particular file extension to be monitored and protected under Ransomware Protection. What setting should the EPM Administrator configure to add the extension?
- Authorized Applications (Ransomware Protection)
- Files to be Ignored Always
- Anti-tampering Protection
- Default Policies
Correct answer: A
Question 40
If Privilege Management is not working on an endpoint, what is the most likely cause that can be verified in the EPM Agent Log Files?
- Behavior of the elevation prompt for administrators in Admin Approval Mode is set to “Prompt for Consent for non-Windows binaries”.
- Agent version is incompatible.
- UAC policy Admin Approval for the Built-in Administrator Account is set to “Disabled”.
- UAC policy Run all administrators in Admin Approval Mode is set to “Enabled”.
Correct answer: D
Question 41
How does a Trusted Source policy affect an application?
- Applications will be allowed to run and will only elevate if required.
- Applications will be allowed to run and will inherit the process token from the EPM agent.
- Applications will be allowed to run always in elevated mode.
- Application from the defined trusted sources must be configured on a per applicationbasis, in order to define run and elevation parameters.
Correct answer: A
Question 42
When deploying EPM and in the Privilege Management phase what is the purpose of Discovery?
- To identify all non-administrative events
- To identify all administrative level events
- To identify both administrative and non-administrative level events
- To identify non-administrative threats
Correct answer: C
Question 43
Which user or group will not be removed as part of CyberArk EPM's Remove Local Administrators feature?
- Built-in Local Administrator
- Domain Users
- Admin Users
- Power Users
Correct answer: A
Question 44
What is the CyberArk recommended practice when deploying the EPM agent to non-persistent VDIs?
- A separate set
- a VDI advanced policy
- a separate license
- A separate computer group
Correct answer: A
Question 45
How does CyberArk EPM's Ransomware Protection feature monitor for Ransomware Attacks?
- It compares known ransomware signatures retrieved from virus databases.
- It sandboxes the suspected ransomware and applies heuristics.
- It monitors for any unauthorized access to specified files.
- It performs a lookup of file signatures against VirusTotal's database.
Correct answer: C
Question 46
On the Default Policies page, what are the names of policies that can be set as soon as EPM is deployed?
- Privilege Escalation, Privilege Management, Application Management
- Privilege Management, Application Control, Threat analysis
- Privilege Management, Threat Protection, Application Escalation Control
- Privilege Management, Privilege Threat Protection, Local Privileged Accounts Management
Correct answer: D
Question 47
What are valid policy options for JIT and elevation policies?
- Grant temporary access for all users, Policy name, Restart administrative processes in admin approval mode, Collect audit information
- Grant temporary access for, Policy name, Terminate administrative processes when the policy expires, Collect audit information
- Grant administrative access, Policy name, Log off to apply policy, Collect policy violation information
- Terminate administrative services, Grant policy access for, Policy name, Collect audit reports
Correct answer: B
Question 48
An application has been identified by the LSASS Credentials Harvesting Module.
What is the recommended approach to excluding the application?
- In Agent Configurations, add the application to the Threat Protection Exclusions.
- Add the application to the Files to be Ignored Always in Agent Configurations.
- Exclude the application within the LSASS Credentials Harvesting module.
- Add the application to an Advanced Policy or Application Group with an Elevate policy action.
Correct answer: A
Question 49
If you want to diagnose agent EPM agent connectivity issues, what is the agent executable that can be used from the command line?
- vf_agent.exe
- epm_agent.exe
- vault_agent.exe
- db_agent.exe
Correct answer: A
Question 50
What unauthorized change can CyberArk EPM Ransomware Protection prevent?
- Windows Registry Keys
- Website Data
- Local Administrator Passwords
- Certificates in the Certificate Store
Correct answer: D
Question 51
An end user is reporting that an application that needs administrative rights is crashing when selecting a certain option menu item. The Application is part of an advanced elevate policy and is working correctly except when using that menu item.
What could be the EPM cause of the error?
- The Users defined in the advanced policy do not include the end user running the application.
- The Advanced: Time options are not set correctly to include the time that the user is running the application at.
- The Elevate Child Processes option is not enabled.
- The Specify permissions to be set for selected Services on End-user Computers is set to Allow Start/Stop
Correct answer: C
Question 52
What are Trusted sources for Windows endpoints used for?
- Creating policies that contain trusted sources of applications.
- Defining applications that can be used by the developers.
- Listing all the approved application to the end users.
- Managing groups added by recommendation.
Correct answer: C
Question 53
What feature is designed to exclude applications from CyberArk EPM's Ransomware Protection, without whitelisting the application launch?
- Trusted Sources
- Authorized Applications (Ransomware Protection)
- Threat Intelligence
- Policy Recommendations
Correct answer: B
Question 54
An EPM Administrator would like to notify end users whenever the Elevate policy is granting users elevation for their applications. Where should the EPM Administrator go to enable the end-user dialog?
- End-user UI in the left panel of the console
- Advanced, Agent Configurations
- Default Policies
- End-User UI within the policy
Correct answer: D
Question 55
A Helpdesk technician needs to provide remote assistance to a user whose laptop cannot connect to the Internet to pull EPM policies. What CyberArk EPM feature should the Helpdesk technician use to allow the user elevation capabilities?
- Offline Policy Authorization Generator
- Elevate Trusted Application If Necessary
- Just In Time Access and Elevation
- Loosely Connected Devices Credential Management
Correct answer: A
Question 56
What EPM component is responsible for communicating password changes in credential rotation?
- EPM Agent
- EPM Server
- EPM API
- EPM Discovery
Correct answer: A
Question 57
An end user is experiencing performance issues on their device after the EPM Agent had been installed on their machine. What should the EPM Administrator do first to help resolve the issue?
- Verify any 3rd party security solutions have been added to EPM's Files To Be Ignored Always configuration and CyberArk EPM has also been excluded from the 3rd party security solutions.
- Enable the Default Policy's Privilege Management Control, Unhandled Privileged Applications in Elevate mode.
- Rerun the agent installation on the user's machine to repair the installation.
- Uninstall or disable any anti-virus software prohibiting the EPM Agent functionalities.
Correct answer: D
Question 58
What are the policy targeting options available for a policy upon creation?
- AD Users and Groups, Computers in AD Security Groups, Servers
- Computers in this set, Computers in AD Security Groups, Users and Groups
- OS Computers, EPM Sets, AD Users
- EPM Sets, Computers in AD Security Groups, AD Users and AD Security Groups
Correct answer: D
Question 59
What type of user can be created from the Threat Deception LSASS Credential Lures feature?
- It does not create any users
- A standard user
- A local administrator user
- A domain admin user
Correct answer: C
Question 60
An EPM Administrator would like to exclude an application from all Threat Protection modules. Where should the EPM Administrator make this change?
- Privilege Threat Protection under Policies.
- Authorized Applications under Application Groups.
- Protect Against Ransomware under Default Policies.
- Threat Protection under Agent Configurations.
Correct answer: B
Question 61
Which threat intelligence source requires the suspect file to be sent externally?
- NSRL
- Palo Alto Wildfire
- VirusTotal
- CyberArk Application Risk Analysis Service (ARA)
Correct answer: B
Question 62
Can the EPM Set Administrator configure Audit Dialog Pop-ups for the Record Audit Video option?
- Yes, when Audit Video recording started, when Audit Video recording stopped, and when Audit Recording video reached size limit.
- Yes, when Audit Video recording started, when not enough disk space to start the video recording, and when video recording is initializing.
- Yes, when Audit Video recording started, when Audit Video recording is uploaded to the EPM server, and when audit recording cannot be initialized.
- No, Audit Video is only available without the possibility of having End-User dialog pop-ups.
Correct answer: B
Question 63
You need to upgrade Windows EPM agents when agent self-defense is enforced.
How can you accomplish this? (Choose two.)
- Upgrade the EPM Agent from the EPM management console.
- In Agent Configuration settings, disable agent self-defense and upgrade the agents through the EPM Management console or a software distribution tool.
- Deploy the MSI and include the secure token as a parameter in the MSI.
- Download the latest EPM Agent MSI and installation key and deploy the agent with a software distribution tool.
- Unzip the TAR file and run install.sh.
Correct answer: BC
Question 64
After how many days will events be removed from event management?
- 14
- 30
- 90
- 365
Correct answer: C
Question 65
As a help desk support team member, you are trying to scan specific computers to discover the applications installed on them.
Which statements about scans are correct? (Choose two.)
- Scans can be performed on a computer once every 24 hours.
- Folders can be scanned using the scan, EPM agent files, and components.
- Scans can be performed on computers that are currently being scanned.
- Scans cannot be performed on disconnected machines.
- Scans can be performed on disconnected machines.
Correct answer: BD
Question 66
After how many days is customer data, including backup data, deleted automatically after the expiration or termination of CyberArk EPM services or sets?
- 30
- 45
- 60
- 90
Correct answer: C
Question 67
Arrange the steps to implement Privilege Management in the correct sequence.
Correct answer: To work with this question, an Exam Simulator is required.
Question 68
Which action does CyberArk EPM execute for applications categorized as “Trusted Sources”?
- Block applications.
- Exclude from the CyberArk EPM policy enforcement.
- Always elevate the permissions of the applications.
- Elevate the permissions when required.
Correct answer: B
Question 69
Which functions are part of the Local Privileged Accounts Management default policy? (Choose two.)
- Remove local administrators.
- Rotate credentials of local privileged user accounts.
- Automatically onboard local privileged user accounts.
- Create credential lures to detect and deceive attackers.
- Protect against user-created local privileged user accounts.
Correct answer: BC
Question 70
A CyberArk EPM administrator wants to include a specific file extension to be monitored and protected under Ransomware Protection.
Which setting should the administrator configure to add the extension?
- Authorized Applications (Ransomware Protection)
- Files to be Ignored Always
- Anti-tampering Protection
- Default Policies
Correct answer: D
Question 71
CyberArk EPM’s Ransomware Protection must be set to which mode to prevent ransomware?
- Detect
- Block
- Restrict
- Deny
Correct answer: B
Question 72
Which types of reports does CyberArk EPM support?
- Events, Policies, Admin audits
- Events, Policies, Endpoints, Admin audits
- Events, Policies
- Events, Policies, Endpoints, Admin audits, Set Audits
Correct answer: D
Question 73
Which information is collected from CyberArk EPM administrators? (Choose two.)
- local usernames and groups.
- EPM username (email address)
- IP address from which the administrator is connected
- hardware specifications
- launched applications
Correct answer: BC
Question 74
A set administrator is creating 100 custom groups to manage the application of policies based on computers within a set. Your organization provided a CSV file containing the list of computers and custom groups. Now you need to import and manage these custom groups in a set.
How do you enable the feature to import the groups?
- Turn on the Synchronize computer groups parameter under Set configuration.
- Turn on the Import computer groups parameter under Agent configuration.
- Turn on the Manage computer groups parameter under Set configuration.
- Turn on the Create computer groups parameter under Agent configuration.
Correct answer: C
Question 75
What must be provided to disable the EPM agent self-defense on an endpoint?
- Installation Key
- Agent ID
- Agent Self-Defense Password
- Secure Token
Correct answer: C
Question 76
Which port or protocol does the EPM Agent use to communicate with the EPM SaaS?
- ТСР1815
- HTTP
- TCP443
- UDP1815
Correct answer: C
Question 77
Match each Aggregated Event type to the correct description.
Correct answer: To work with this question, an Exam Simulator is required.
Question 78
What is the filename for the service and log parameters for the Linux Endpoint in CyberArk EPM?
- config.yaml and agentparams.yaml
- agentparams.yaml and agentiogs.yaml
- agentservices.yaml and agentlogs.yaml
- agentservices.yaml and config.yaml
Correct answer: A
Question 79
In Automatic SAML User Provisioning, which attribute name must be added for all users who will log into CyberArk EPM using SAML?
- EPM-User
- EPM-User-Binding
- EPM-SAML-Binding
- EPM-SAML
Correct answer: A
Question 80
What is required to install and run the CyberArk EPM admin utility?
- Begin sudo to see groups and users in /etc/passwd
- Stop the password rotation
- Ensure NET 4.8 or higher was installed on the endpoint
- Install the EPM agent before running the utility.
Correct answer: C
Question 81
Arrange the policy action in the correct priority order beginning with the policy action with the highest priority.
Correct answer: To work with this question, an Exam Simulator is required.
Question 82
Which statements are correct about Trusted Sources in CyberArk EPM? (Choose two.)
- They are limited to applications with a specific digital signature.
- They cannot apply retroactively if the application is moved to a different location.
- An unhandled application is an application that is not specifically trusted or blocked in the organization
- They can include applications located in a specific network share
- They can incorporate applications installed by them, even with different digital signatures
Correct answer: CD
Question 83
Match each task with the appropriate installation method.
Correct answer: To work with this question, an Exam Simulator is required.
Question 84
Which policy actions are applied in the Trust Policies for Windows and MacOS Endpoints? (Choose two.)
- Allow
- Elevate If Necessary
- Trusted
- Elevate
- Elevate if need child process
Correct answer: AC
Question 85
What best describes the purpose of the Policy Recommendations feature?
- suggest least privilege policies based on application usage patterns and behavior
- automatically block high-risk applications without user input
- enforce mandatory security updates for all endpoint devices
- recommend software upgrades for outdated applications
Correct answer: A
Question 86
What are application policy actions within CyberArk EPM? (Choose two.)
- Run As Administrator
- Elevate if Necessary
- Prevent Launch as Needed
- Authorized Sources
- Elevate
Correct answer: BE
Question 87
What is a CyberArk EPM policy that can be created to detect an attempt to escalate privileges by harvesting credentials without alerting the potential attacker?
- Application Groups set to Block, report on attempt to run
- Remove Local Administrators, report on attempt to run elevated programs
- Ransomware, define Authorized Applications, report on all other applications
- Privilege Deception, set to Detect, review all attempts
Correct answer: D
Question 88
You are an IT team member. An end user reported an issue with the Visual Studio application. As part of troubleshooting, you want to suspend policies and test the application. You would like to apply the setting to one endpoint.
What is the path to create this configuration?
- Configuration → Set Configuration → Agent Configuration → General Configuration → Edit parameters
- Configuration → Agent Configuration → Set Configuration → General Configuration → Edit parameters
- Configuration → Agent Configuration → Create custom Configuration
- Configuration → User access tokens → Create custom Configuration
Correct answer: B
Question 89
Which parameters can be enabled for data collection by the agent? (Choose two.)
- Event queue flush period
- Collect unprotected accounts
- Policy audit event flush period
- Push active policies to agents
- Automate report generation
Correct answer: AC
Question 90
Which agent parameter defines protection from third-party DLLs on Windows?
- agent self-defense
- protect elevated processes from DLL hijacking
- anti-tampering protection
- protect administrative user groups
Correct answer: B
Question 91
What are default out-of-the-box predefined Application groups? (Choose two.)
- Elevate
- Stopped
- Elevate if necessary
- Developer applications
- Allowed sources
Correct answer: DE
Question 92
A set administrator wants to download the immediate enforcement agent for Windows but cannot find the tab in the EPM console's download center.
What is the reason?
- The set is not an immediate enforcement agent set.
- The set administrator does not have account admin permissions.
- The feature is not enabled in the set configuration settings.
- The immediate enforcement agent is downloaded from Marketplace
Correct answer: A
Question 93
Which time format is used for events in EPM reports?
- local time
- UTC+0
- EST
- GMT+5
Correct answer: B
Question 94
In which report will you find secure tokens generated for endpoints in the CyberArk EPM management console?
- Admin Audits
- Endpoints
- Events
- Application Catalog
Correct answer: B
Question 95
When generating a secure token, for which scopes can the secure token be valid? (Choose two.)
- all computers part of an EPM tenant
- all computers part of a set
- a subset of computers part of an EPM tenant
- a subset of computers part of a set
- all computers part of a specific Active Directory organizational unit
Correct answer: BD
Question 96
What does the policy action influence?
- order of precedence
- policy name
- operating system
- application groups
Correct answer: A
Question 97
Match the items to their correct configuration type.
Correct answer: To work with this question, an Exam Simulator is required.
Question 98
What happens during agent installation on MacOS?
- A token is generated
- The user must insert a username and password to apply an upgrade.
- A service account is created and automatically removed at the end of installation.
- A service account is automatically created and must not be deleted.
Correct answer: D
Question 99
Where can you find a detailed list of all of the policies applied to an endpoint?
- Endpoint inventory report in Reports - Endpoint section
- In the Endpoints, My Computers, Active Policies
- C:\Program Files\CyberArk\Endpoint Privilege Manager\Agent\vf_policies.xml
- vf_policy file in the support info bundle
Correct answer: B
Question 100
Which policy category focuses on managing and controlling software permissions within an organization?
- Credential Rotation
- Application Policy
- Privilege Threat Protection
- Script Distribution
Correct answer: B
Question 101
For some reason, a few machines were disconnected from the console and are having problems connecting to the console. Now, the Intune team is trying to uninstall agents, but self-defense is enabled on these machines.
What is the best way to uninstall the EPM agents under these circumstances?
- Turn off self-defense, then the Intune team can uninstall the agent
- Generate a secure token for all computers and use it for this machine.
- Generate a secure token for any of the alive machines and use it for this machine.
- Turn off self-defense for this specific machine by creating a custom configuration, so the Intune team can uninstall the agent.
Correct answer: A
Question 102
What is the primary purpose of CyberArk CORA AI?
- Provide real-time antivirus protection for applications.
- Recommend policy actions based on machine learning algorithms.
- Manage user credentials and passwords
- Automatically block unauthorized users from accessing the network.
Correct answer: B
Question 103
Which default policy includes the functionality of creating credential lures?
- Privilege Management
- Privilege Threat Protection
- Local Privileged Accounts Management
- Phishing Protection Management
Correct answer: B
Question 104
Which statements are correct regarding a non-persistent VDI set? (Choose two.)
- Only network and operating system data are reported
- Credential rotation policies cannot be configured.
- You cannot create a policy with a specific computer name
- Only limited manual computer groups can be created
- Custom user access tokens cannot be created
Correct answer: AC
Question 105
As part of the IT team, you enabled auditing to record an end user's activities in the cmd application. When checking for a video file on an end user's computer, you found that it was deleted due to the default retention period. Now, you are trying to set the maximum retention period.
What is the maximum retention period that can be set?
- 60 days
- 90 days
- 1 year
- 2 years
Correct answer: D
Question 106
In the CyberArk EPM SaaS console, which feature displays the percentage of detected applications handled?
- Application Groups
- Policy Recommendations
- Application Coverage by Policies
- Policy Audit
Correct answer: C
Question 107
Which statements about Privilege Threat Protection are correct? (Choose two.)
- It only supports credential types for Windows OS and Web Browsers
- It can detect and block credential theft for critical operating system resources.
- It cannot create credential lures to deceive attackers
- It helps prevent lateral movement to stop attack vectors.
- It is limited to detecting threats in IT Applications only
Correct answer: BD
Question 108
Which types of data are collected by CyberArk EPM endpoints? (Choose two.)
- computer name
- file explorer information
- EPM username (email address)
- installed programs
- administrator's IP address
Correct answer: AD
Question 109
If an EPM agent loses connectivity to the EPM SaaS, what will occur?
- The EPM agent continues to apply policies based on the last policies retrieved
- The EPM agent automatically disables its agent self-defense
- The EPM SaaS attempts to redeploy the agent to the endpoint.
- The EPM SaaS redirects the EPM agent to an available EPM SaaS region
Correct answer: A
Question 110
Which statements about the Immediate Enforcement (IE) agent are correct? (Choose two.)
- Threat protection is not available for IE agents.
- The agent installation kit for IE agents does not contain the set’s policies.
- IE agents are available for Windows. MacOS and Linux.
- IE agents should be installed in the same set as regular agents
- "Download immediate enforcement agent" must be set to ON when deploying an IE agent
Correct answer: AE
Question 111
For some reason, Windows executables are not scanned in the scanning process.
Where should you check to determine whether the file type is being selected?
- Configuration → Agent Configuration → General Configuration → File Types to Scan for Application Catalog
- Configuration → Server Configuration → General Configuration → File Types to Scan for Application Catalog
- Configuration → Set Configuration → Agent Configuration → File Types to Scan for Application Catalog
- Configuration → Agent Configuration → Set Configuration → File Types to Scan for Application Catalog
Correct answer: A
Question 112
Arrange the policy names and their priority in the correct order of precedence.
Correct answer: To work with this question, an Exam Simulator is required.
Question 113
Which action is required after adding driver-level exclusions for CybeArk EPM?
- Reboot the endpoint
- Restart the EPM service.
- Manually update EPM settings.
- Delete temporary files.
Correct answer: A
Question 114
Which statements are correct about the functions of the Application Catalog? (Choose two.)
- It detects applications that are managed by policies and those that are not
- Threat analyses can be run on application events.
- An event can be deleted before the retention period ends
- You can configure the number of displayed events in the Application Catalog up to 1000 events
- It detects only events for applications that are not managed by policies.
Correct answer: AD
Question 115
How does the "Create Credential Lures" function detect and deceive attackers?
- It creates employees with fake phone numbers in the company employee directory; when an attacker calls the fake phone number. EPM creates an event.
- It creates LinkedIn profiles of real employees with easy to guess passwords, when an attacker attempts to log in to the profile. EPM creates an event.
- It creates user credentials in popular places on the endpoint; when an attacker attempts to log into the user. EPM creates an event.
- It creates fake accounts in CyberArk's privileged access management vault, when an attacker attempts to use the account, EPM creates an event.
Correct answer: C
Question 116
Arrange the steps to manage unsigned macOS executables in the correct sequence.
Correct answer: To work with this question, an Exam Simulator is required.
Question 117
Arrange the steps to install the agent on a new macOS endpoint in the correct sequence.
Correct answer: To work with this question, an Exam Simulator is required.
Question 118
Which methods does CyberArk EPM SaaS use to secure data? (Choose two.)
- data encryption using SSL/TLS and AES-256
- regular data backups to external servers
- access control through SAML authentication
- data segregation to ensure customer data isolation
- blockchain technology for data integrity
Correct answer: AD
Question 119
A CyberArk EPM administrator wants to enable CyberArk EPM's Ransomware Protection in Restrict mode.
What should the administrator do?
- Set Block unhandled applications to On.
- Set Protect Against Ransomware to Restrict
- Set Protect Against Ransomware to Restrict and Set Block unhandled applications to On.
- Set Control unhandled applications to Detect
Correct answer: C
Question 120
How long can a JIT policy can be granted to a user of the target resource?
- 10 minutes to 48 hours
- 1 to 24 hours
- 1 to 72 hours
- unlimited time range
Correct answer: A
Question 121
You are a CyberArk EPM Administrator creating a new Application Blocked dialog with these end-user requirements:
- ability to provide reasons to the CyberArk EPM Administrator to access the blocked application on a per request basis
- ability to notify the end-users upon approval completion.
Which sections enable these requirements? (Choose two.)
- User Email Request
- Action Buttons
- User Justification Request
- Main message
- Application Properties
Correct answer: AC
Question 122
Which types of sets are defined by their license type?
- regular machines and non-persistent VDI machines
- non-persistent VDI machines and full protection set
- credentials rotation and regular machines
- full protection set and credentials rotation set.
Correct answer: B
Question 123
Which types of reports are available in the CyberArk EPM Management Console? (Choose two.)
- Endpoints
- Policies
- Ransomware
- Domain Users
- Error Logs
Correct answer: AC
Question 124
What is the function of the group "Microsoft Windows Programs (default Policies)"?
- monitors or restricts access to sensitive resources for Microsoft Windows programs
- groups Microsoft Windows programs for easy management
- monitors the use of Windows programs for license management
- allows Windows applications to provide access to sensitive resources
Correct answer: A
HOW TO OPEN VCE FILES
Use VCE Exam Simulator to open VCE files

HOW TO OPEN VCEX AND EXAM FILES
Use ProfExam Simulator to open VCEX and EXAM files


ProfExam at a 20% markdown
You have the opportunity to purchase ProfExam at a 20% reduced price
Get Now!




